Getting User Roles and Rights
Your Logi application may need to use any security Roles or Rights availableas part of the SecureKey information. Various security-related elements are used for this purpose, as follows:
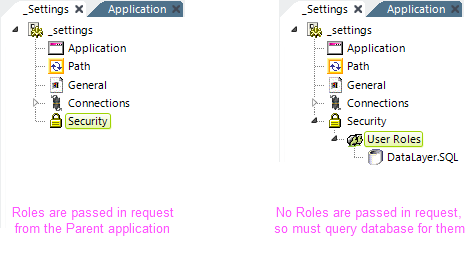
If user Roles information is included in the SecureKey request from the Parent application (as described in Configuring the Parent Application), then subsequent report requests will cause that information to be automatically available in the Security element, as shown above, left.
If user Roles information is not included in the SecureKey request but is desired, it can still be retrieved from a datasource, using a User Roles element and a datalayer, as shown above, right. The data returned into the datalayer should have either a Role value in the first column of each row, or be a single row with one column containing multiple Roles in a comma-delimited list.
If user Rights information is included in the SecureKey request from the Parent application (as described in Configuring the Parent Application), then subsequent report requests will cause that information to also be automatically available in the Security element.
If user Rights information is not included in the SecureKey request but is desired, it can be retrieved in several ways, all of which begin with the addition of the User Rights element:
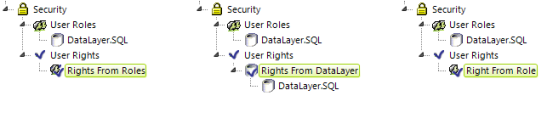
The examples shown above include a User Roles element, but it's not necessary if Roles are supplied to the Security element via the SecureKey request. The separate techniques and elements used to retrieve the Rights are described below:
These elements may be used in any combination; the Rights
retrieved by each are combined together into a comprehensive rights list.