Cloudera and Kerberos Authentication
Logi Info has been certified with Cloudera's CDH4 using Kerberos as a method to authenticate database access. Hortonworks is not certified at this time.
Kerberos security should be enabled at the cluster server by following the instructions on the Cloudera web site. MIT's kfw-4.0.1-amd64.msi must be installed on the Logi application web server, and then the file krb5.conf should copied from the Kerberos server to the web server. Save it to the following folder and change its file extension as shown: C:\ProgramData\MIT\Kerberos5\krb5.ini.
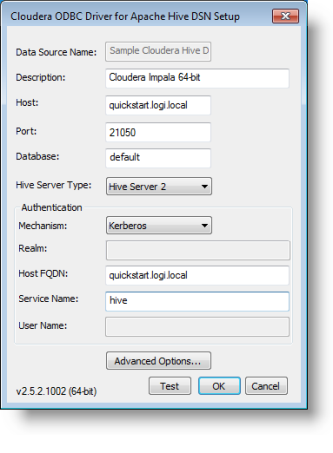
A typical DSN setup is shown above. ![]() Kerberos will
not work with IP addresses in place of a Host name.
Kerberos will
not work with IP addresses in place of a Host name.
For this example, a Hadoop account was created for "logixml" and added to the Kerberos domain ("CLOUDERA"). Then this account is used in the Impala configuration to allow access as the Kerberos principal user.
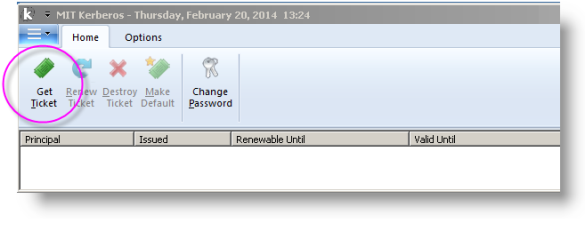
The MIT Kerberos Ticket Manager utility, which is part of the kfw-4.0.1-amd64.msi installation and shown above, is used to get a Kerberos ticket.
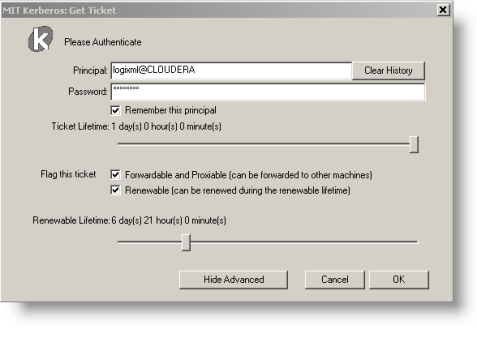
On the server, the MIT Kerberos Get Ticket application is used to obtain the correct credentials from the Kerberos domain controller.
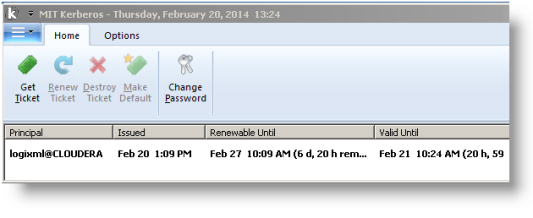
Once the credentials are obtained, they appear in the Ticket Manager, as shown above.