Server Security System
Logi Report Server protects all of the resources (objects in the resource tree or version tables, such as folders, resources, and archive versions) using a security system. This system maintains a registered set of users and sets permissions on each resource for each user. This topic describes the server security system.
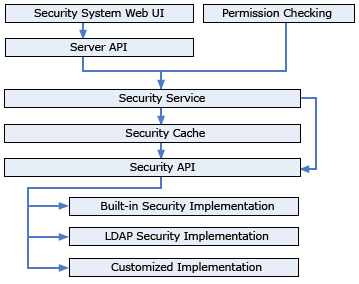
The Logi Report Server implements its runtime security checking system based on a standard set of Security Service method calls. The default implementation is based on the data set of users and resources in Logi Report Server.
For integration with an existing application that already has a system for managing users and permissions, Logi Report Server defines the Security Service as a Java interface and enables an application developer to supply a customized version to replace the default implementation. This enables an existing application to provide a custom version of the Security Service that supports Logi Report Server runtime security checking based on user data and permissions that are stored outside Logi Report Server. In this configuration, the Logi Report Server admin section for managing users and permissions is not used.
Logi Report Server also can integrate with an existing application that uses an LDAP system for managing user and group information. Logi Report Server can be configured to interact with the LDAP system so that edit of information about users and groups can be done only in the LDAP system. Information about permissions for resources is not part of the LDAP data model. That information continues to be maintained by Logi Report Server.
Accessing user and permission data by database look-up on each service request may result in many time-consuming IO operations. As a result, the performance of the server security system may be lowered. In order to promote performance, a cache system exists just above the Security Service. The cache system is used to store security objects including users, groups, roles, and access control lists obtained from making calls to the Security Service. This cached data will be used when the same information is needed later.
The following diagram illustrates the Logi Report Server security system structure:
Select the following links to view the topics:
- Security System Data Model
- Multitenancy Supported via Organizations
- Role Based Security
- Security Cache System
- Using an LDAP Server's Security System
For more information, see Customized Implementation of the Security API and Seamless Integrated Security Solution.
 Previous Topic
Previous Topic