Configuring the LDAP Server
To use an LDAP server's security system, you should first enable Logi JReport Server to adapt to a directory server. You can configure either via UI or with the LDAPProperties.xml file.
Currently the following directory servers are supported: Novell Directory Server, Microsoft Site Server, iPlanet Directory Server, Active Directory Advanced Server, Lotus Domino Server and OpenLDAP Directory Server. If you need access to a different directory server, contact your Logi JReport Sales Representative. New servers are frequently being added.
Below is a list of the sections covered in this topic:
Configuring via UI
To configure the LDAP server via UI, on the Logi JReport Administration Page, go to the Configuration > LDAP > Server tab, then specify the following options as required.
The following presents examples for adapting Logi JReport Server to specific directory servers:
Example 1: Configuration for adapting to a Novell Directory Server
Example 2: Configuration for adapting to a Microsoft Site Server
Example 3: Configuration for adapting to an iPlanet Directory Server
Example 4: Configuration for adapting to the Active Directory Advanced Server
Example 5: Configuration for adapting to a Lotus Domino Server on NT
Example 6: Configuration for adapting to an OpenLDAP Directory Server
Example 1: Configuration for adapting to a Novell Directory Server
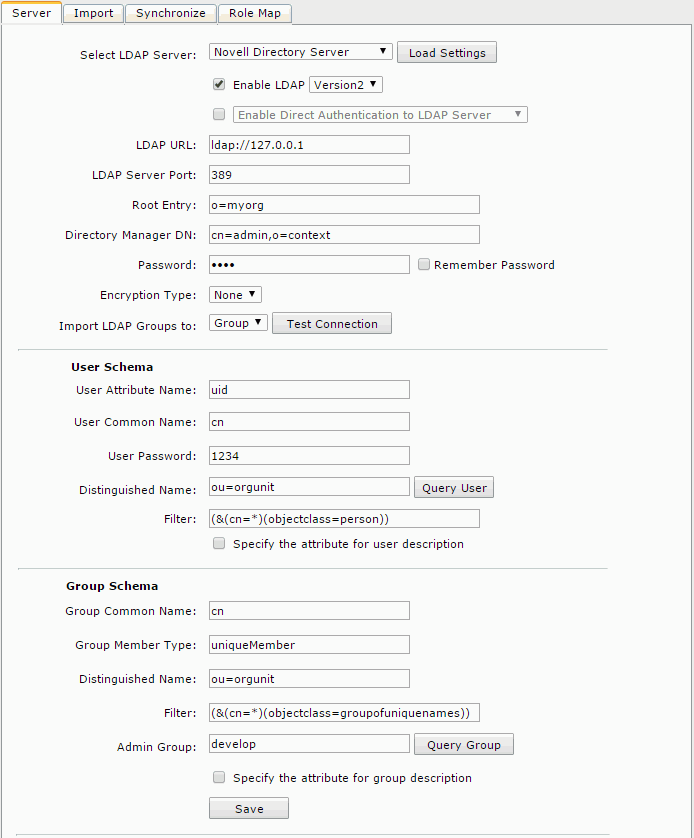
- Select Novell Directory Server from the Select LDAP Server drop-down list, and then select Load Settings. The settings of the Novell Directory Server will then be loaded.
- Check the Enable LDAP checkbox, and input the following information:
- LDAP URL: ldap://IP address or host name of your Novell Directory Server (for example:
ldap://127.0.0.1) - LDAP Server Port: 389
- Root Entry: o=the name of the root (for example: o=myorg)
- Directory Manager DN: cn=user name of the directory manager,o=context (for example: cn=admin,o=context)
- Password: the password of the Directory Manager (for example: 1234)
- Encryption Type: None
- Import LDAP Groups to: Group
- User Schema
- Distinguished Name: ou=the name of the organization unit where you want to perform a search for users (for example: ou=orgunit)
- Filter: (&(cn=the filter criteria that you want to set )(objectclass=person)) (for example: (&(cn=*)(objectclass=person)))
- Group Schema
- Distinguished Name: ou=the name of the organization unit that you want to perform a search for groups (for example: ou=orgunit)
- Filter: (&(cn=the filter criteria that you want to set )(objectclass=groupofuniquenames)) (for example: (&(cn=*)(objectclass=groupofuniquenames)))
- Admin Group: The name of the group you want to add to the Admin group (for example: develop)
- LDAP URL: ldap://IP address or host name of your Novell Directory Server (for example:
- You can test the connection settings by selecting the Test Connection button, get the query result of the users specified in the option Filter by selecting the Query User button, and get the query result of groups specified in the option Filter by selecting the Query Group button.
- Select Save to save all settings. You can then get all users and groups from the orgunit organizational unit.
Example 2: Configuration for adapting to a Microsoft Site Server
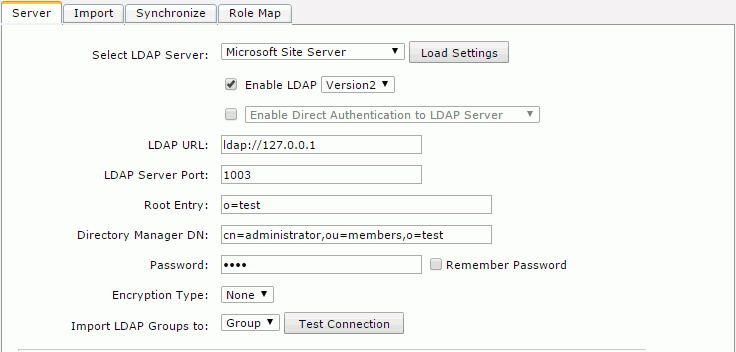
- Select Microsoft Site Server from the Select LDAP Server drop-down list, and then select Load Settings. The settings of the Microsoft Site Server will be loaded.
- Make sure that the Enable LDAP checkbox is selected, and input the following information:
- LDAP URL: ldap://IP address or host name of your Microsoft site Server (for example:
ldap://127.0.0.1) - LDAP Server Port: 1003
- Root Entry: o=test
- Directory Manager DN: cn=administrator,ou=members,o=test
- Password: test
- Encryption Type: None
- Import LDAP Groups to: Group
- LDAP URL: ldap://IP address or host name of your Microsoft site Server (for example:
- Select Save to save all settings in this page.
You can then get all users from the members organizational unit and all groups from the groups organizational unit.
Example 3: Configuration for adapting to an iPlanet Directory Server
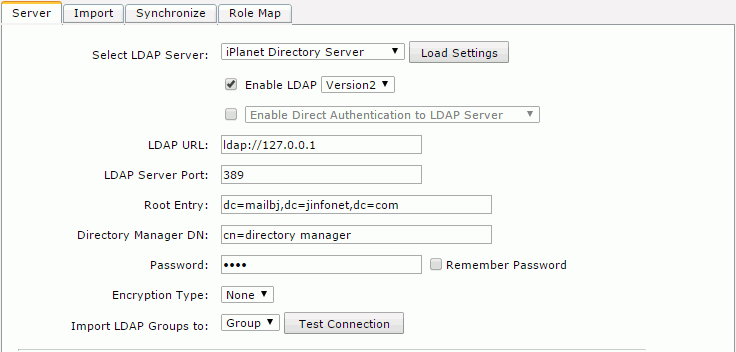
- Select iPlanet Directory Server from the Select LDAP Server drop-down list, and then select Load Settings. The settings of iPlanet Directory Server will then be loaded.
- Make sure that the Enable LDAP checkbox is selected, and input the following information:
- LDAP URL: ldap://IP address of your iPlanet Directory Server
- LDAP Server Port: 389
- Root Entry: dc=mailbj,dc=jinfonet,dc=com
- Directory Manager DN: cn=directory manager
- Password: jinfonet
- Encryption Type: None
- Import LDAP Groups to: Group
- Select Save to save all the settings in this page. You can then get all users in the people organizational unit and all groups in the groups organizational unit.
Example 4: Configuration for adapting to the Active Directory Advanced Server
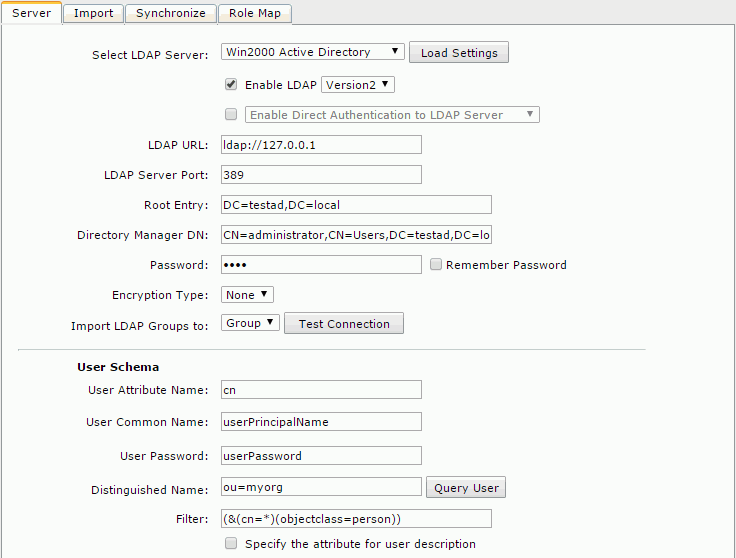
- Select Win2000 Active Directory from the Select LDAP Server drop-down list, and then select Load Settings. The settings are then cleared and you can input your information.
- Make sure that the Enable LDAP checkbox is selected, and input the following information:
- LDAP URL: ldap://IP address of your Windows 2000 Advanced Server
- LDAP Server Port: 389
- Root Entry: DC=testad,DC=local
- Directory Manager DN: CN=administrator,CN=Users,DC=testad,DC=local
- Password: 1234
- Encryption Type: None
- Import LDAP Groups to: Group
- User Schema
- User Attribute Name: cn
- User Common Name: userPrincipalName
- User Password: userPassword
- Distinguished Name: ou=myorg
- Filter: (&(cn=*)(objectclass=person))
- Group Schema
- Group Common Name: cn
- Group Member Type: member
- Distinguished Name: ou=myorg
- Filter: (&(cn=*)(objectclass=group))
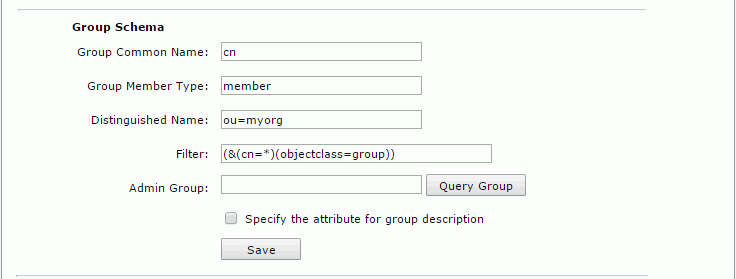
- Select Save to save all settings in this page. You can then get all users and groups from the myorg organizational unit.
Example 5: Configuration for adapting to a Lotus Domino Server on NT
- Select Lotus Domino on NT from the Select LDAP Server drop-down list, and then select Load Settings. The settings are then cleared and you can input your information.
- Make sure that the Enable LDAP checkbox is selected, and input the following information:
- LDAP URL: ldap://IP address of your Lotus Domino Server
- LDAP Server Port: 389
- Root Entry:
- Directory Manager DN: cn=admin,o=jtotal
- Password: 123456
- Encryption Type: None
- Import LDAP Groups to: Group
- User Schema
- User Attribute Name: uid
- User Common Name: cn
- User Password: userPassword
- Distinguished Name: ou=developer, o=jtotal
- Filter: (&(cn=*)(objectclass=person))
- Group Schema
- Group Common Name: cn
- Group Member Type: member
- Distinguished Name:
- Filter: (&(cn=*)(objectclass=groupofnames))
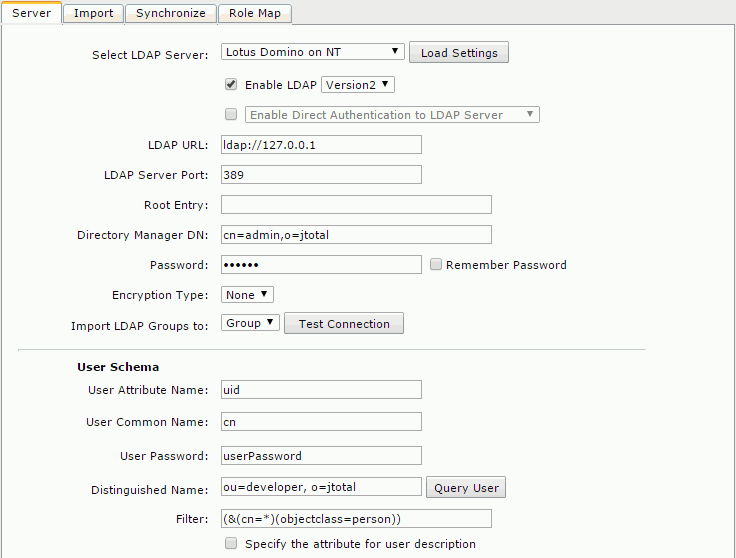
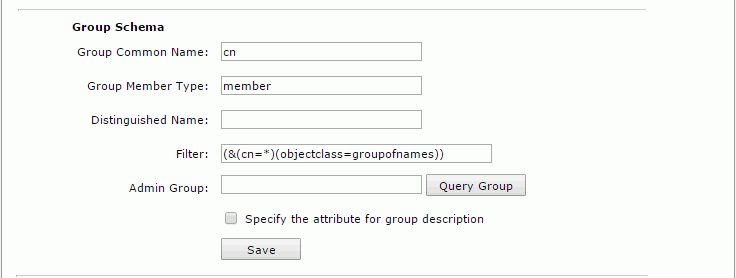
- Select Save to save all settings in this page. You can then get all users and groups from the developer organization unit.
Example 6: Configuration for adapting to an OpenLDAP Directory Server
- Select OpenLDAP Directory Server from the Select LDAP Server drop-down list, and then select Load Settings. The settings are then cleared and you can input your information.
- Make sure that the Enable LDAP checkbox is selected, and input the following information:
- LDAP URL: ldap://IP address of your OpenLDAP Directory Server (for example:
ldap://127.0.0.1) - LDAP Server Port: 389
- Root Entry: dc=openldap, dc=ldaptest
- Directory Manager DN: cn=Manager,dc=openldap,dc=ldaptest
- Password: 123456789
- Encryption Type: None
- Import LDAP Groups to: Group
- User Schema
- User Attribute Name: uid
- User Common Name: cn
- User Password: userPassword
- Distinguished Name: ou=members
- Filter: (&(uid=*)(objectclass=person))
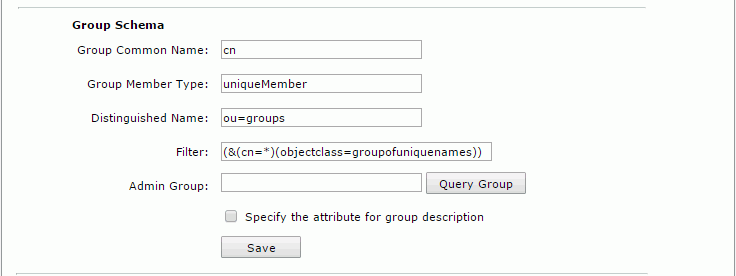
- Group Schema
- Group Common Name: cn
- Group Member Type: uniqueMember
- Distinguished Name: ou=groups
- Filter: (&(cn=*)(objectclass=groupofuniquenames))
- Admin Group:
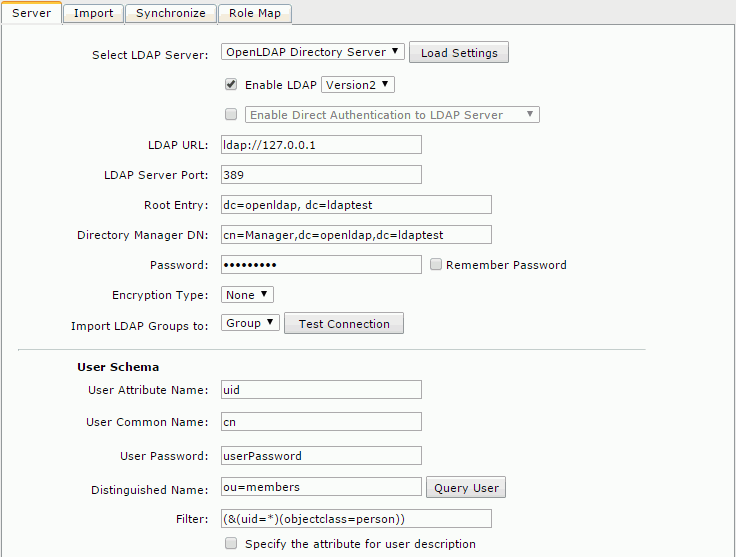
- LDAP URL: ldap://IP address of your OpenLDAP Directory Server (for example:
- Select Save to save all settings in this page. You can then get all users and groups from the developer organization unit.
Notes:
- Make sure that the Directory Manager DN is a user with prior LDAP Server permission, and who can retrieve other LDAP users.
- Make sure that the users and groups you want to query and import into Logi JReport Server belong to the organization you typed into the Distinguished Name field.
Configuring With LDAPProperties.xml
The file LDAPProperties.xml located in <install_root>\properties can be used for LDAP server configuration. The properties in the file can be mapped to the options in the Server tab on the Logi JReport Administration > Configuration > LDAP page. For details about the usages of the properties, refer to that of the mapped options.
| UI Option | Properties in LDAPProperties.xml |
|---|---|
| Enable LDAP | enableLDAPSupport |
| Version2/Version3 | ldapVersion |
| Enable Direct Authentication to LDAP Server | enableNoneImportedLDAPSupport |
| Enable Auto-Import of Users from LDAP Server | enableAutoImportLDAPUser |
| LDAP URL | url |
| LDAP Server Port | serverPort |
| Root Entry | rootEntry |
| Directory Manager DN | directoryManagerDN |
| Password | password |
| Encryption Type | isUsingSSL |
| Import LDAP Groups to | importGroupType |
| User Attribute Name | userAN |
| User Common Name | userCN |
| User Password | userPassword |
| Distinguished Name | userDN |
| Filter (for user schema) | userFilter |
| Specify the attribute for user description | userEnableSAN |
| Attribute Name (for user schema) | userSAN |
| Group Common Name | groupCN |
| Group Member Type | groupMemeberType |
| Distinguished Name | groupDN |
| Filter (for group schema) | groupFilter |
| Admin Group | groupAdminGroup |
| Specify the attribute for group description | groupEnableSAN |
| Attribute Name (for group schema) | groupSAN |
Troubleshooting LDAP Server Configuration
When you encountered any problems during the LDAP configuration, refer to the following for help.
LDAP configuration failure resulting in re-login failure as an admin user
An admin user may fail to carry out LDAP configuration properly, and thus then cannot log onto the Logi JReport Administration page to manage the server. If this happens, you should follow the below steps:
- Modify the property in the LDAP configuration XML file LDAPProperties.xml in
<install_root>\propertiesas follows to turn off the Enable Direct Authentication to LDAP Server option:<env-enableNoneImportedLDAPSupport>false</env-enableNoneImportedLDAPSupport> - Restart Logi JReport Server and log in as a built-in security admin user to correct the LDAP configuration.
Warning messages in the advent of incorrect LDAP configuration
Apart from the notes offered on the Logi JReport Administration > Configuration > LDAP page, prompt warning information is also provided in order to cope with incorrect LDAP configuration. The server system will prompt warning messages in the following cases:
- If you do not fill in the Admin Group field or specify an admin group.
- If the admin group specified does not hold a user.
- If the admin group specified does not exist in the LDAP server.
 Previous Topic
Previous Topic
 Back to top
Back to top